“ Installing and Configuring Windows Server 2012 ” Exam 70-410. Here you can get the latest free Microsoft MCSA 70-410 exam exercise questions and answers for free and easily improve your skills!
70-410 exam – This exam is part one of a series of three exams that test the skills and knowledge necessary to implement a core
Windows Server 2012 infrastructure in an existing enterprise environment. Passing this exam validates a candidate’s ability to implement and configure Windows Server 2012 core services, such as Active Directory and the networking services.
Passing this exam along with the other two exams confirms that a candidate has the skills and knowledge necessary for implementing,
managing, maintaining, and provisioning services and infrastructure in a Windows Server 2012 environment. Follow the link to find more information about https://www.leads4pass.com/70-410.html exam.
Watch the Microsoft MCSA 70-410 video tutorial online
Table of Contents:
- Latest Microsoft 70-410 pdf
- Test your Microsoft 70-410 exam level
- Related 70-410 Popular Exam resources
- Get leads4pass Coupons (12% OFF)
- What are the advantages of leads4pass?
Latest Microsoft 70-410 pdf
[PDF] Free Microsoft MCSA 70-410 pdf dumps download from Google Drive: https://drive.google.com/open?id=1JBHUP0X7mq_vqacwDdz5KJyZIKirsO49
Free Microsoft 70-410 Exam Practice Questions
QUESTION 1
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 has the virtual switches listed in
the following table.
You create a virtual machine named VM1. VM1 has two network adapters. One network adapter connects to vSwitch1.
The other network adapter connects to vSwitch2.You configure NIC teaming on VM1.
You need to ensure that if a physical NIC fails on Server1, VM1 remains connected to the network.
What should you do on Server1?
A. Run the Set-VmNetworkAdapterIsolation cmdlet.
B. Add a new network adapter to VM1.
C. Modify the properties of the network adapters on VM1.
D. Modify the properties of vSwitch1 and vSwitch2.
E. Modify the properties of the network adapters on VM1.
F. Run the Set-VmNetworkAdapterAdapterFailoverConfiguration cmdlet.
Correct Answer: C
References: https://www.altaro.com/hyper-v/work-hyper-v-virtual-network-adapters/
QUESTION 2
Your network contains an Active Directory domain named contoso.com.
The password policy for the domain is set to require a minimum password length of 10 characters.
A user named User1 and a user named User2 work for the sales department.
User1 is forced to create a domain password that has a minimum of 12 characters. User2 is forced to create a domain
password that has a minimum of eight characters.
You need to identify what forces the two users to have different password lengths.
Which tool should you use?
A. Credential Manager
B. Security Configuration Wizard (SCW)
C. Group Policy Management
D. Active Directory Administrative Center
Correct Answer: D
In Windows Server 2008, you can use fine-grained password policies to specify multiple password policies and apply
different password restrictions and account lockout policies to different sets of users within a single domain. For
example, to increase the security of privileged accounts, you can apply stricter settings to the privileged accounts and
then apply less strict settings to the accounts of other users. Or in some cases, you may want to apply a special
password policy for accounts whose passwords are synchronized with other data sources.
This is found in the Active Directory Administrative Center. You can use Active Directory Administrative Center to
perform the following Active Directory administrative tasks:
Create new user accounts or manage existing user accounts Create new groups or manage existing groups Create new
computer accounts or manage existing computer accounts Create new organizational units (OUs) and containers or
manage existing OUs Connect to one or several domains or domain controllers in the same instance of Active Directory
Administrative Center, and view or manage the directory information for those domains or domain controllers Filter
Active Directory data by using query-building search
QUESTION 3
Your network contains a Hyper-V host named Hyperv1 that runs Windows Server 2012 R2. Hyperv1 has a virtual switch
named Switch1.
You replace all of the network adapters on Hyperv1 with new network adapters that support single-root I/O virtualization
(SR-IOV). You need to enable SR-IOV for all of the virtual machines on Hyperv1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. On each virtual machine, modify the Advanced Features settings of the network adapter.
B. Modify the settings of the Switch1 virtual switch.
C. Delete, and then recreate the Switch1 virtual switch.
D. On each virtual machine, modify the BIOS settings.
E. On each virtual machine, modify the Hardware Acceleration settings of the network adapter.
Correct Answer: CE
QUESTION 4
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed.
An iSCSI SAN is available on the network.
Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4.
You create a LUN on the SAN to host the virtual hard drive files for the virtual machines.
You need to create a 3-TB virtual hard disk for VM1 on the LUN. The solution must prevent VM1 from being paused if
the LUN runs out of disk space.
Which type of virtual hard disk should you create on the LUN?
A. Dynamically expanding VHDX
B. Fixed-size VHDX
C. Fixed-size VHD
D. Dynamically expanding VHD
Correct Answer: B
The virtual disk needs to be a VHDX file since it is going to be over 2TB in size and it must be fixed-size so that the
space is already taken on the server (that way the server does not run out of space as the volume grows) even if the
actual virtual disk does not yet hold that amount of data.
QUESTION 5
Your network contains two Active Directory forests named adatum.com and contoso.com. Both forests contain multiple
domains. A two-way trust exists between the forests. The contoso.com domain contains a domain local security group
named Group1. Group1 contains contoso\user1 and adatum\user1.
You need to ensure that Group1 can only contain users from the contoso.com domain.
Which three actions should you perform?
To answer, move three actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: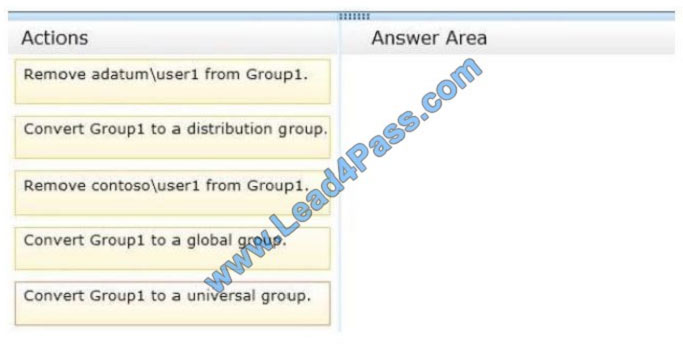
Correct Answer:
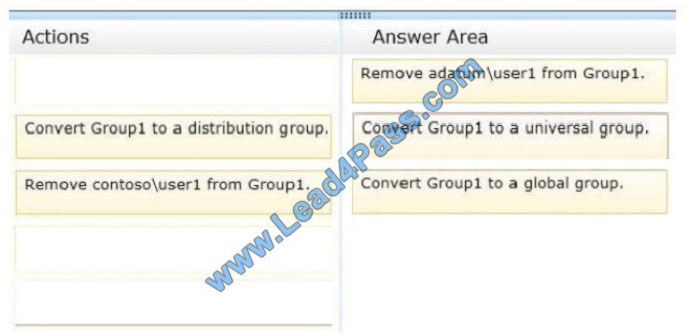
Domain local Groups that are used to grant permissions within a single domain. Members of domain local groups can
include only accounts (both user and computer accounts) and groups from the domain in which they are defined.
———– to review. Universal groups can only include objects from its own forest Groups can have — domain local, built-in
local, global, and universal. That is, the groups have different areas in different scopes which they are valid.
A domain local group is a security or distribution group that can contain universal groups, global groups, other domain
local groups from its own domain, and accounts from any domain in the forest. You can give domain local security
groups
rights and permissions on resources that reside only in the same domain where the domain local group is located. A
global group is a group that can be used in its own domain, in member servers and in workstations of the domain, and
in
trusting domains. In all those locations, you can give a global group rights and permissions and the global group can
become a member of local groups. However, a global group can contain user accounts that are only from its own
domain. A
universal group is a security or distribution group that contains users, groups, and computers from any domain in its
forest as members. You can give universal security groups rights and permissions on resources in any domain in the
forest.
Universal groups are not supported.
Domain local -Groups that are used to grant permissions within a single domain. Members of domain local groups can
include only accounts (both user and computer accounts) and groups from the domain in which they are defined. Built-
in
local – Groups that have a special group scope that have domain local permissions and, for simplicity, are often referred
to as domain local groups. The difference between built-in local groups and other groups is that built-in local groups
can’t
be created or deleted. You can only modify built-in local groups. References to domain local groups apply to built-in
local groups unless otherwise noted. Global – Groups that are used to grant permissions to objects in any domain in the
domain tree or forest. Members of global groups can include only accounts and groups from the domain in which they
are defined. Universal – Groups that are used to grant permissions on a wide scale throughout a domain tree or forest.
Members of global groups include accounts and groups from any domain in the domain tree or forest.
Global to universal. This conversion is allowed only if the group that you want to change is not a member of another
global scope group.
Domain local to universal. This conversion is allowed only if the group that you want to change does not have another
domain local group as a member.
Universal to global. This conversion is allowed only if the group that you want to change does not have another
universal group as a member.
Universal to domain local. There are no restrictions for this operation.
QUESTION 6
You have a server named Server1 that runs Windows Server 2012 R2.
You need to perform the following storage configuration tasks on Server1:
Bring a disk named Diskl online.
Defragment a volume named Volumel.
Remove a disk named Disk2 from a storage pool named Pooll.
Which cmdlet should you use to perform each task?
To answer, drag the appropriate cmdlets to the correct tasks. Each cmdlet may be used once, more than once, or not at
all. You may need to drag the split bar between panes or scroll to view content.
Select and Place: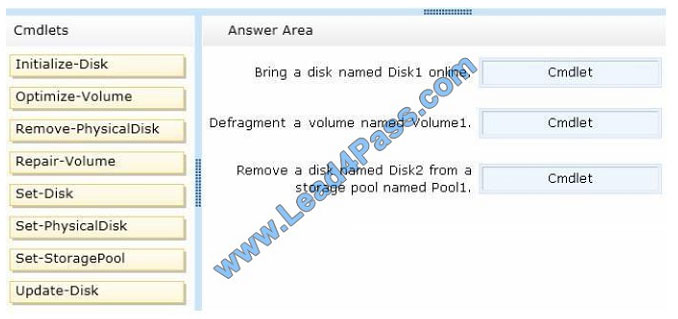
Correct Answer:
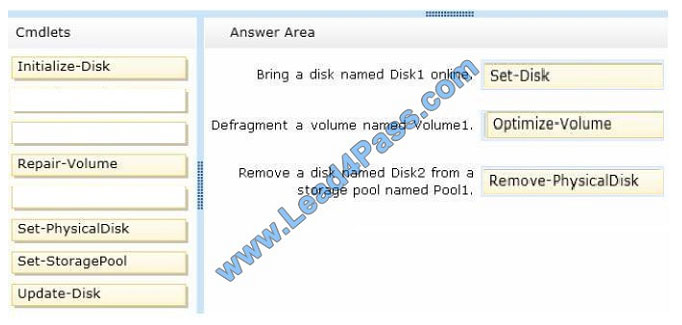
QUESTION 7
Your network contains an Active Directory domain named adatum.com. The domain contains a file server named
Server2 that runs Windows Server 2012 R2. Server2 contains a shared folder named Home. Home contains the home
folder of
each user.
All users have the necessary permissions to access only their home folder.
A user named User1 opens the Home share as shown in the exhibit. (Click the Exhibit button.)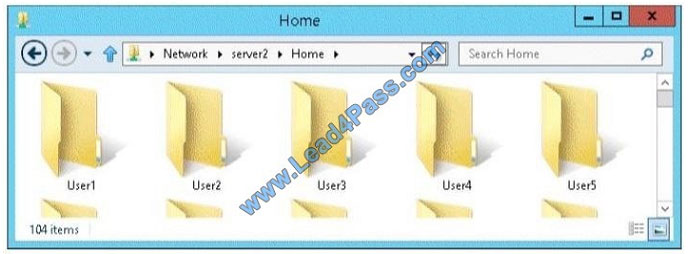
You need to ensure that all users see only their own home folder when they access Home.
What should you do from Server2?
A. From Windows Explorer, modify the properties of Home.
B. From Server Manager, modify the properties of the volume that contains Home.
C. From Windows Explorer, modify the properties of the volume that contains Home.
D. From Server Manager, modify the properties of Home.
Correct Answer: D
Access-based Enumeration is a new feature included with Windows Server 2003 Service Pack 1. This feature based file
servers to list only the files and folders to which they have allows users of Windows Server 2003 access when browsing
content on the file server. This eliminates user confusion that can be caused when users connect to a file server and
encounter a large number of files and folders that they cannot access. Access-based Enumeration filters the list of
available files and folders on a server to include only those that the requesting user has access to. This change is
important because this allows users to see only those files and directories that they have access to and nothing else.
This mitigates the scenario where unauthorized users might otherwise be able to see the contents of a directory even
though they don\\’t have access to it.
QUESTION 8
Your network contains an Active Directory forest. The forest contains a single domain named contoso.com. The domain
contains four domain controllers. The domain controllers are configured as shown in the following table.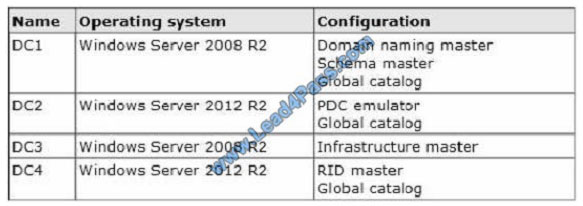
All domain controllers are DNS servers.
You plan to deploy a new domain controller named DC5 in the contoso.com domain.
You need to identify which domain controller must be online to ensure that DC5 can be promoted successfully to a
domain controller.
Which domain controller should you identify?
A. DC1
B. DC2
C. DC3
D. DC4
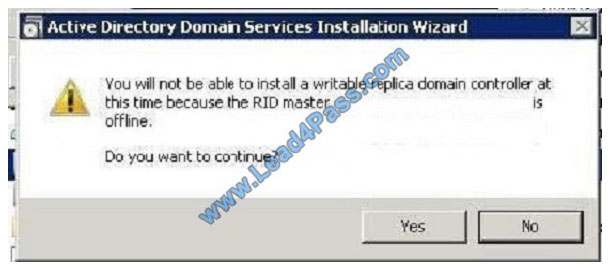
Correct Answer: D
Relative ID (RID) Master: Allocates active and standby RID pools to replica domain controllers in the same domain.
(corp.contoso.com). Must be online for newly promoted domain controllers to obtain a local RID pool that is required to
advertise or when existing domain controllers have to update their current or standby RID pool allocation. The RID
master is responsible for processing RID pool requests from all domain controllers in a particular domain. When a DC
creates a security principal object such as a user or group, it attaches a unique Security ID (SID) to the object. This SID
consists of a domain SID (the same for all SIDs created in a domain), and a relative ID (RID) that is unique for each
security principal SID created in a domain. Each DC in a domain is allocated a pool of RIDs that it is allowed to assign to
the security principals it creates. When a DC\\’s allocated RID pool falls below a threshold, that DC issues a request for
additional RIDs to the domain\\’s RID master. The domain RID master responds to the request by retrieving RIDs from
the domain\\’s unallocated RID pool and assigns them to the pool of the requesting DC At any one time, there can be
only one domain controller acting as the RID master in the domain.
The Infrastructure Master ?The purpose of this role is to ensure that cross-domain object references are correctly
handled. For example, if you add a user from one domain to a security group from a different domain, the Infrastructure
Master makes sure this is done properly. As you can guess however, if your Active Directory deployment has only a
single domain, then the Infrastructure Master role does no work at all, and even in a multi-domain environment it is
rarely used except when complex user administration tasks are performed, so the machine holding this role doesn\\’t
need to have much horsepower at all.
QUESTION 9
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server
2012 R2.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
You need to ensure that when users log on to Server1, their user account is added automatically to a local group named
Group1 during the log on process.
Which Group Policy settings should you modify?
A. User Rights Assignment
B. Preferences
C. Security Options
D. Restricted Groups
Correct Answer: B
With Preferences, local and domain accounts can be added to a local group without affecting the existing members of
the group
References:
Training Guide: Installing and Configuring Windows Server 2012 R2: Chapter 8: File Services and Storage, p. 361.
http://technet.microsoft.com/en-us/library/cc785631(v=ws.10).aspx
http://www.grouppolicy.biz/2010/01/how-to-use-group-policy-preferences-to-secure-local-administrator-groups/
http://technet.microsoft.com/en-us/library/cc780182(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/hh831424.aspx
QUESTION 10
Catalog Servers. Your domain structure contains one root domain and one child domain. You modify the folder
permissions on a file server that is in the child domain. You discover that some Access Control entries start with
S-1-5-21 and that no account name is listed.
You need to list the account names. What should you do?
A. Move the RID master role in the child domain to a domain controller that holds the Global Catalog.
B. Modify the schema to enable replication of the friendly names attribute to the Global Catalog.
C. Move the RID master role in the child domain to a domain controller that does not hold the Global Catalog.
D. Move the infrastructure master role in the child domain to a domain controller that does not hold the Global Catalog.
Correct Answer: D
If the IM Flexible Single Master Operation (FSMO) role holder is also a global catalog server, the phantom indexes are
never created or updated on that domain controller. (The FSMO is also known as the operations master.) This behavior
occurs because a global catalog server contains a partial replica of every object in Active Directory. The IM does not
store phantom versions of the foreign objects because it already has a partial replica of the object in the local global
catalog.
For this process to work correctly in a multi domain environment, the infrastructure FSMO role holder cannot be a global
catalog server. Be aware that the first domain in the forest holds all five FSMO roles and is also a global catalog.
Therefore, you must transfer either role to another computer as soon as another domain controller is installed in the
domain if you plan to have multiple domains.
QUESTION 11
Your company has a main office and two branch offices. The offices connect to each other by using a WAN link.
In the main office, you have a server named Server1 that runs Windows Server 2012 R2.
Server1 is configured to use an IPv4 address only.
You need to assign a multicast IPv6 address to Server1.
Which IPv6 address should you assign to Server1?
A. fd00:ab32:14:ad88:ac:58:abc2:4
B. 2001:ab32:145c::32cc:401b
C. fe80:ab32:145c::32cc:401b
D. ff00:3fff:65df:145c:dca8::82a4
Correct Answer: D
References: https://technet.microsoft.com/pt-pt/library/cc757359(v=ws.10).aspx
QUESTION 12
Your network contains an Active Directory domain named contoso.com.
You need to prevent users from installing a Windows Store app named App1.
What should you create?
A. An application control policy executable rule
B. An application control policy packaged app rule
C. A software restriction policy certificate rule
D. An application control policy Windows Installer rule
Correct Answer: B
Windows 8 is coming REALLY SOON and of course one of the big new things to computer with that is the new
Packaged Apps that run in the start screen. However, these apps are very different and do not install like traditional
apps to a path or have a true “executable” file to launch the program. Of course enterprises need a way to control these
packaged apps and therefore Microsoft has added a new feature Packaged Apps option to the App1ocker feature.
Packaged apps (also known as Windows 8 apps) are new to Windows Server 2012 R2 and Windows 8. They are based
on the new app model that ensures that all the files within an app package share the same identity. Therefore, it is
possible to control the entire Application using a single App1ocker rule as opposed to the non-packaged apps where
each file within the app could have a unique identity. Windows does not support unsigned packaged apps which implies
all packaged apps must be signed. App1ocker supports only publisher rules for Packaged apps. A publisher rule for a
packaged app is based on the following information: Publisher of the package Package name Package version
Therefore, an App1ocker rule for a Packaged app controls both the installation as well as the running of the app.
Otherwise, the publisher rules for Packaged apps are no different than the rest of the rule collections; they support
exceptions, can be increased or decreased in scope, and can be assigned to users and groups.
QUESTION 13
Your network contains an Active Directory domain named contoso.com. The domain contains 20 computer accounts
that reside in an organizational unit (OU) named OU1.
A Group Policy object (GPO) named GPO1 is linked to OU1. GPO1 is used to assign several user rights to a user
named User1.
In the Users container, you create a new user named User2.
You need to ensure that User2 is assigned the same user rights as User1 on all of the client computers in OU1.
What should you do?
A. Modify the settings in GPO1.
B. Modify the link of GPO1.
C. Link a WMI filter to GPO1.
D. Move User2 to OU1.
Correct Answer: D
The GPO is linked to OU1. By moving User2 to OU1 the GPO will be applied to this user.
Related 70-410 Popular Exam resources
Get leads4pass Coupons(12% OFF)
What are the advantages of leads4pass?
leads4pass employs the most authoritative exam specialists from Microsoft, Cisco, CompTIA, IBM, EMC, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader! Choose leads4pass to pass the exam with ease!
Summarize:
It’s not easy to pass the Microsoft 70-410 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. leads4pass provides you with the most relevant learning materials that you can use to help you prepare.