
CyberOps Professional 350-201 certification is one of the most popular Cisco certifications! Moderate difficulty!
To help candidates successfully pass the 350-201 CBRCOR (Performing CyberOps Using Cisco Security Technologies) certification exam, we provide the best 350-201 certification exam solution:
Use Lead4Pass 350-201 dumps: https://www.leads4pass.com/350-201.html (139 Q&A), with PDF and VCE learning formats, to help you easily study and pass the CyberOps Professional 350-201 certification exam.
You can also get early access to some of the 350-201 exam practice questions:
| From | Number of exam questions | Exam name | Exam code |
| Lead4Pass | 15 | Performing CyberOps Using Cisco Security Technologies (CBRCOR) | 350-201 |
Question 1:
After a recent malware incident, the forensic investigator is gathering details to identify the breach and its causes. The investigator has isolated the affected workstation. What is the next step that should be taken in this investigation?
A. Analyze the applications and services running on the affected workstation.
B. Compare workstation configuration and asset configuration policy to identify gaps.
C. Inspect registry entries for recently executed files.
D. Review audit logs for privilege escalation events.
Correct Answer: C
Question 2:

Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
A. exploitation
B. actions on objectives
C. delivery
D. reconnaissance
Correct Answer: C
Reference: https://www2.deloitte.com/content/dam/Deloitte/sg/Documents/risk/sea-risk-cyber-101-july2017.pdf
Question 3:
Employees report computer system crashes within the same week. An analyst is investigating one of the computers that crashed and discovers multiple shortcuts in the system\’s startup folder. It appears that the shortcuts redirect users to malicious URLs.
What is the next step the engineer should take to investigate this case?
A. Remove the shortcut files
B. Check the audit logs
C. Identify affected systems
D. Investigate the malicious URLs
Correct Answer: C
Question 4:
What is the HTTP response code when the REST API information requested by the authenticated user cannot be found?
A. 401
B. 402
C. 403
D. 404
E. 405
Correct Answer: A
Question 5:
The incident response team was notified of the detected malware. The team identified the infected hosts, removed the malware, restored the functionality and data of infected systems, and planned a company meeting to improve the incident handling capability.
Which step was missed according to the NIST incident handling guide?
A. Contain the malware
B. Install IPS software
C. Determine the escalation path
D. Perform vulnerability assessment
Correct Answer: D
Question 6:
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization\’s service area. What are the next steps the engineer must take?
A. Assign the issue to the incident handling provider because no suspicious activity has been observed during business hours.
B. Review the SIEM and FirePower logs, block all traffic, and document the results of calling the call center.
C. Define the access points using StealthWatch or SIEM logs, understand services being offered during the hours in question, and cross-correlate other source events.
D. Treat it as a false positive, and accept the SIEM issue as valid to avoid alerts from triggering on weekends.
Correct Answer: A
Question 7:
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS. Which type of cloud environment should be used?
A. IaaS
B. PaaS
C. DaaS
D. SaaS
Correct Answer: A
Question 8:
Which bash command will print all lines from the “colors.txt” file containing the non-case-sensitive pattern “Yellow”?
A. grep -i “yellow” colors.txt
B. locate “yellow” colors.txt
C. locate -i “Yellow” colors.txt
D. grep “Yellow” colors.txt
Correct Answer: A
Question 9:
An engineer has created a bash script to automate a complicated process. During script execution, this error occurs permission is denied. Which command must be added to execute this script?
A. chmod +x ex. sh
B. source ex. sh
C. chroot ex. sh
D. sh ex. sh
Correct Answer: A
Reference: https://www.redhat.com/sysadmin/exit-codes-demystified
Question 10:
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days. Having the names of the 3 destination countries and the user\’s working hours, what must the analyst do next to detect an abnormal behavior?
A. Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
B. Create a rule triggered by 1 successful VPN connection from any nondestination country
C. Create a rule triggered by multiple successful VPN connections from the destination countries
D. Analyze the logs from all countries related to this user during the traveling period
Correct Answer: D
Question 11:
A security manager received an email from an anomaly detection service, that one of their contractors has downloaded 50 documents from the company\’s confidential document management folder using a company-owned asset al039-ice4ce687TL0500. A security manager reviewed the content of downloaded documents and noticed that the data affected is from different departments. What are the actions a security manager should take?
A. Measure the confidentiality level of downloaded documents.
B. Report to the incident response team.
C. Escalate to the contractor\’s manager.
D. Communicate with the contractor to identify the motives.
Correct Answer: B
Question 12:
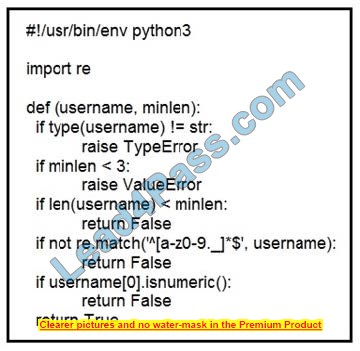
Refer to the exhibit. An organization is using an internal application for printing documents that requires a separate registration on the website. The application allows format-free user creation, and users must match these required conditions to comply with the company\’s user creation policy: minimum length: 3 usernames can only use letters, numbers, dots, and underscores usernames cannot begin with a number
The application administrator has to manually change and track these days to ensure compliance. An engineer is tasked to implement a script to automate the process according to the company user creation policy. The engineer implemented this piece of code within the application, but users are still able to create format-free usernames.
Which change is needed to apply the restrictions?
A. modify code to return error on restrictions def return false_user(username, miles)
B. automate the restrictions def automate_user(username, miles)
C. validate the restrictions, def validate_user(username, miles)
D. modify code to force the restrictions, def force_user(username, miles)
Correct Answer: B
Question 13:
An organization had a breach due to a phishing attack. An engineer leads a team through the recovery phase of the incident response process. Which action should be taken during this phase?
A. Host a discovery meeting and define the configuration and policy updates
B. Update the IDS/IPS signatures and reimage the affected hosts
C. Identify the systems that have been affected and tools used to detect the attack
D. Identify the traffic with data capture using Wireshark and review email filters
Correct Answer: C
Question 14:
What is the limitation of cyber security risk insurance?
A. It does not cover the costs to restore stolen identities as a result of a cyber attack
B. It does not cover the costs to hire forensics experts to analyze the cyber attack
C. It does not cover the costs of damage done by third parties as a result of a cyber attack
D. It does not cover the costs to hire a public relations company to help deal with a cyber attack
Correct Answer: A
Reference: https://tplinsurance.com/products/cyber-risk-insurance/
Question 15:
A threat actor has crafted and sent a spear-phishing email with what appears to be a trustworthy link to the site of a conference that an employee recently attended. The employee clicked the link and was redirected to a malicious site through which the employee downloaded a PDF attachment infected with ransomware. The employee opened the attachment, which exploited vulnerabilities on the desktop. The ransomware is now installed and is calling back to its command and control server.
Which security solution is needed at this stage to mitigate the attack?
A. web security solution
B. email security solution
C. endpoint security solution
D. network security solution
Correct Answer: D
…
Learn some of the latest 350-201 exam questions and answers online to help you assess your current strength with online practice!
Now, download the latest CyberOps Professional 350-201 certification exam solution: https://www.leads4pass.com/350-201.html, including 139 latest exam questions and answers!
Choose any 350-201 dumps PDF or 350-201 dumps VCE to help you practice 350-201 certification exam questions easily and ensure you pass the exam 100%.