Best CyberOps Professional 350-201 Certification Exam Solution

In the rapidly evolving cybersecurity landscape, professionals capable of conducting forensic analysis, interpreting multi-layered log data, and responding to complex incidents are becoming indispensable. The Cisco CyberOps Professional 350-201 (CBRCOR) certification remains one of the most respected credentials for proving real-world security analysis skills—far more practical than many theory-heavy certifications.
What truly sets this exam apart is its focus on hands-on interpretation of evidence. Security leaders often say:
“Anyone who passes the 350-201 exam is someone who can immediately jump into incident response.”
This comprehensive guide, updated with the latest 2025–2026 Cisco information, helps you prepare effectively, understand new exam trends, and plan your learning path with real-value tools and strategies.
📌 Table of Contents
- Latest Updates for 350-201 (Cisco 2025 Official Notes)
- Exam Structure & Scope (Updated Blueprint)
- Why the 350-201 Certification Is Highly Recognized
- Practical and Efficient Study Strategy (Expert-Backed)
- Essential Tools You Must Know (Real Corporate Use Cases)
- Exam Trends Prediction for 2025–2026 + Career Outlook
- Latest CyberOps Professional 350-201 Questions & Answers
- Recommended Resources (Including Leads4Pass)
- Final Summary: How to Pass on the First Attempt
Latest Updates for 350-201 (Cisco 2025 Official Notes)
Cisco’s January 2025 update to the 350-201 CBRCOR exam introduced several modern changes aligned with real SOC workflows and emerging threat patterns:
- Higher emphasis on AI-driven attack detection, such as ML evasion patterns
- Additional content for cloud log analysis (AWS, Azure, GCP)
- Enhanced focus on Cisco XDR and unified incident investigation workflows
- Fewer theoretical questions; more scenario-based forensic analysis
These updates reflect global industry transitions: SOC teams are moving from signature-driven defense to behavior- and data-driven security operations.
Cisco exam reference link:
https://www.cisco.com/site/us/en/learn/training-certifications/exams/cbrcor.html
Exam Structure & Content Scope (Updated Blueprint)
Exam Structure & Content Scope (Cisco 350-201 CBRCOR – Latest v1.2 as of 2025)
Duration: 120 minutes
Format: Multiple-choice, data interpretation (PCAP/logs/dashboards), scenario-based questions
Language: English
Number of questions: ~90–110 (varies)
Official Domains
- 20% Fundamentals (cybersecurity basics, threat landscape, etc.)
- 30% Techniques (forensics, network/host analysis, threat hunting, MITRE ATT&CK, etc.)
- 30% Processes (incident response, SOC operations, investigation procedures)
- 20% Automation (SOAR, APIs, scripting, Cisco security automation tools)
Recent exam trends (2023–2025 candidate reports):
The exam has shifted heavily toward practical, real-world SOC analyst tasks rather than pure theory. Common question types include:
- Analyzing PCAP files to identify C2 beacons, exfiltration, or malware communications
- Reviewing Windows Event Logs (4624/4625 logons, 4688 process creation, PowerShell, lateral movement via RDP/SMB)
- Interpreting SIEM dashboards (Splunk queries, Elasticsearch, or Cisco-like tools) to map kill chain phases
- Correlating indicators to MITRE ATT&CK tactics/techniques/sub-techniques
- Using threat intelligence (STIX/TAXII, open-source feeds) and behavior analytics (UEBA)
- Understanding Cisco tools (SecureX, XDR, Threat Grid, AMP, etc.) in orchestration/response
The shift is clear: you must understand real attack evidence—not textbook descriptions.
Why the 350-201 Certification Is Highly Recognized
Compared to CEH and Security+, 350-201 is considered a practical analyst-level certification. Key reasons why employers value it include:
(1) High proportion of real technical scenarios
Most questions replicate real attack cases such as:
- Early-stage ransomware behavior
- Unauthorized outbound communication
- Email compromise investigation
(2) Strong focus on tools actually used in SOC teams
Examples include:
- Splunk
- Wireshark
- Cisco Secure Endpoint
- XDR dashboards
These tools dominate enterprise SOC workflows.
(3) Direct relevance to mid-senior analyst roles
Many companies use 350-201 as a benchmark for Tier-2 Analysts, Hunters, and IR Engineers.
Practical and Efficient Study Strategy (Expert Backed)
To pass the 350-201 exam efficiently, focus on scenario-driven learning, not chapter memorization.
(1) Build “Log-Driven Thinking”
Practice recognizing anomalies in:
PCAP traffic
DNS
Web outbound logs
Authentication patterns
(2) Learn by Attack Scenarios, Not Topics
Example:
Learn lateral movement as a whole process, not isolated NTLM or SMB concepts.
(3) Daily Mixed Log Training
Work with Windows logs, Syslog, Splunk events, and network captures.
(4) Use Leads4Pass for Scenario Practice (Natural Mention)
Leads4Pass’s updated 350-201 materials include new XDR + cloud log analysis cases, matching 2025–2026 trends. Their scenario-style questions are helpful for sharpening critical thinking.
(Look up “Leads4Pass 350-201” for updated materials.)
(5) Practice Simulation Questions in the Last 2 Weeks
The exam heavily favors real investigation-style questions.
Essential SOC Toolchains You Must Master
Wireshark
Master handshake anomalies, TLS patterns, DNS exfiltration, and beaconing.
Splunk (SPL Queries)
Key queries:
statsrexsearch/whereconditions
Cisco Secure (Endpoint, XDR, Network Analytics)
Increasingly common in 2025 exam versions.
Security Onion
Learn Zeek, Suricata, Elastic dashboards.
Exam Trends Prediction for 2025–2026 + Career Outlook
The cybersecurity threat landscape is accelerating rapidly. Based on industry movement, here are predictions through 2026:
Trend 1: AI-Driven Attacks Become Mainstream
Expect exam questions related to:
- AI-generated phishing
- Automated lateral movement
- ML model evasion
Trend 2: Higher Weight on Cloud Forensics
CloudTrail, Azure Sign-In, and DNS security will become core skills.
Trend 3: Multi-Log Correlation Questions
PCAP + host log + SIEM dashboard combined scenarios are becoming common.
Career Outlook Through 2026
Roles with increasing demand:
- Threat Hunter
- Tier-2 SOC Analyst
- Digital Forensics Specialist
- Incident Response Engineer
350-201 aligns perfectly with these roles and is considered a high-value credential among enterprise SOC teams globally.
Latest CyberOps Professiona 350-201 exam practice questions online test
| From | Number of exam questions | Complete Study Materials |
| leads4pass | 15 | 139 Q&A |
Q1: According to GDPR, what should be done with data to ensure its confidentiality, integrity, and availability?
A. Perform a vulnerability assessment
B. Conduct a data protection impact assessment
C. Conduct penetration testing
D. Perform awareness testing
Correct Answer: B
Q2: What are the next steps the engineer must take?
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization\’s service area.
A. Assign the issue to the incident handling provider because no suspicious activity has been observed during business hours.
B. Review the SIEM and FirePower logs, block all traffic, and document the results of calling the call center.
C. Define the access points using StealthWatch or SIEM logs, understand services being offered during the hours in question, and cross-correlate other source events.
D. Treat it as a false positive, and accept the SIEM issue as valid to avoid alerts from triggering on weekends.
Correct Answer: A
Q3: How does Wireshark decrypt TLS network traffic?
A. with a key log file using per-session secrets
B. using an RSA public key
C. by observing DH key exchange
D. by defining a user-specified decode-as
Correct Answer: A
Reference: https://wiki.wireshark.org/TLS
Q4: Which asset has the highest risk value?
Refer to the exhibit.
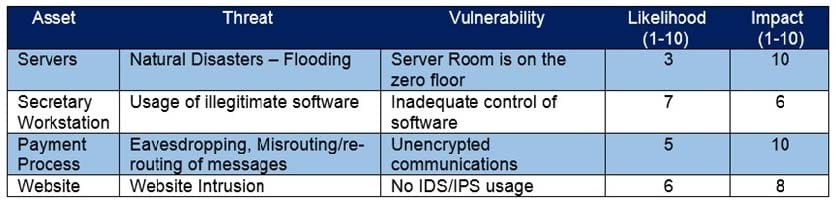
A. servers
B. website
C. payment process
D. secretary workstation
Correct Answer: C
Q5: At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
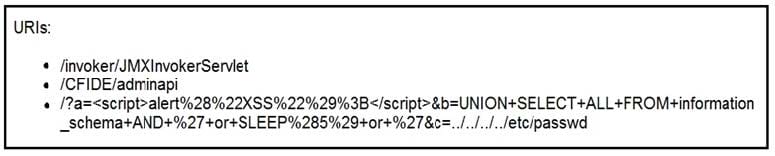
Refer to the exhibit.
A. exploitation
B. actions on objectives
C. delivery
D. reconnaissance
Correct Answer: C
Reference: https://www2.deloitte.com/content/dam/Deloitte/sg/Documents/risk/sea-risk-cyber-101-july2017.pdf
Q6: Which tuning option should be applied to IPS?
A logistic company must use an outdated application located in a private VLAN during the migration to new technologies. The IPS blocked and reported an unencrypted communication.
A. Allow list only authorized hosts to contact the application\’s IP at a specific port.
B. Allow list HTTP traffic through the corporate VLANS.
C. Allow list traffic to application\’s IP from the internal network at a specific port.
D. Allow list only authorized hosts to contact the application\’s VLAN.
Correct Answer: D
Q7: What is a principle of Infrastructure as Code?
A. System maintenance is delegated to software systems
B. Comprehensive initial designs support robust systems
C. Scripts and manual configurations work together to ensure repeatable routines
D. System downtime is grouped and scheduled across the infrastructure
Correct Answer: B
Question 8:
DRAG DROP
Drag and drop the components from the left onto the phases of the CI/CD pipeline on the right.
Select and Place:
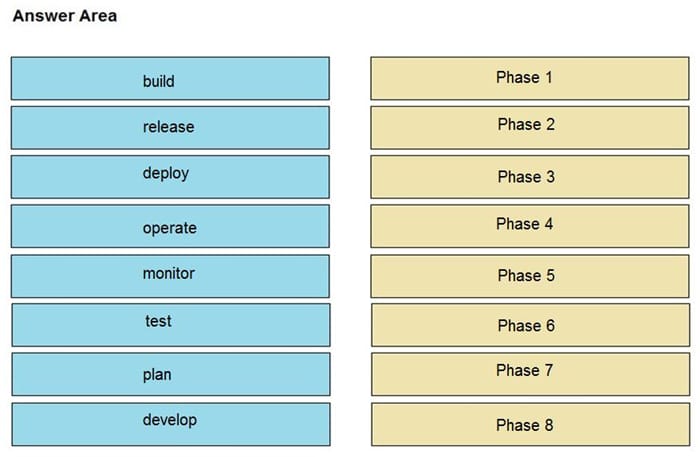
Correct Answer:
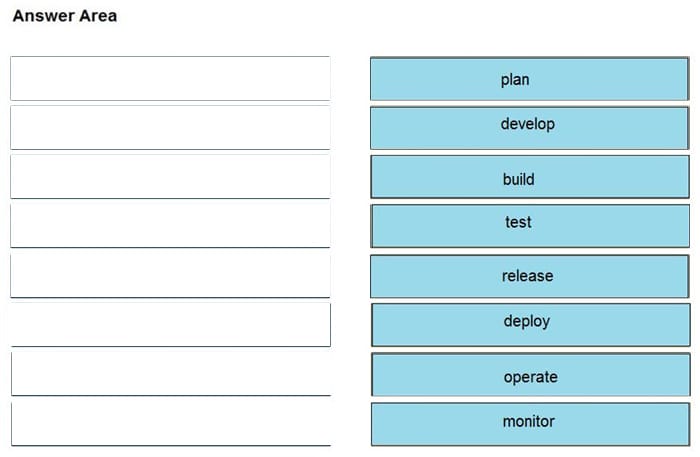
Q9: How is a SIEM tool used?
A. To collect security data from authentication failures and cyber attacks and forward it for analysis
B. To search and compare security data against acceptance standards and generate reports for analysis
C. To compare security alerts against configured scenarios and trigger system responses
D. To collect and analyze security data from network devices and servers and produce alerts
Correct Answer: D
Reference: https://www.varonis.com/blog/what-is-siem/
Q10: Which step was missed according to the NIST incident handling guide?
The incident response team was notified of detected malware. The team identified the infected hosts, removed the malware, restored the functionality and data of infected systems, and planned a company meeting to improve the incident handling capability.
A. Contain the malware
B. Install IPS software
C. Determine the escalation path
D. Perform vulnerability assessment
Correct Answer: D
Q11: Based on the audit, which recommendation should an engineer make for patching?
A company recently completed an internal audit and discovered that there is CSRF vulnerability in 20 of its hosted applications.
A. Identify the business applications running on the assets
B. Update software to patch third-party software
C. Validate CSRF by executing exploits within Metasploit
D. Fix applications according to the risk scores
Correct Answer: D
Q12: Which type of compromise is indicated?
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts overnight.
A. phishing
B. dumpster diving
C. social engineering
D. privilege escalation
Correct Answer: C
Question 13:
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days. Having the names of the 3 destination countries and the user\’s working hours, what must the analyst do next to detect an abnormal behavior?
A. Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
B. Create a rule triggered by 1 successful VPN connection from any nondestination country
C. Create a rule triggered by multiple successful VPN connections from the destination countries
D. Analyze the logs from all countries related to this user during the traveling period
Correct Answer: D
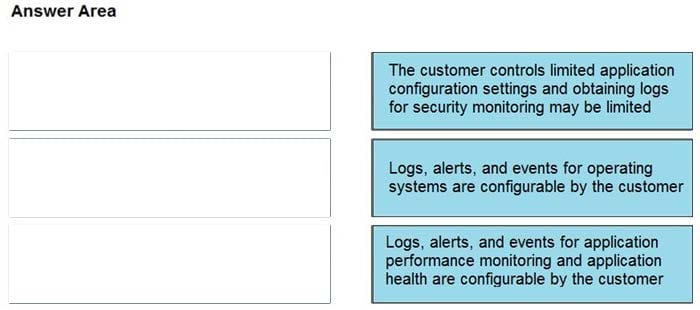
Question 14:
DRAG DROP
Drag and drop the telemetry-related considerations from the left onto their cloud service models on the right.
Select and Place:
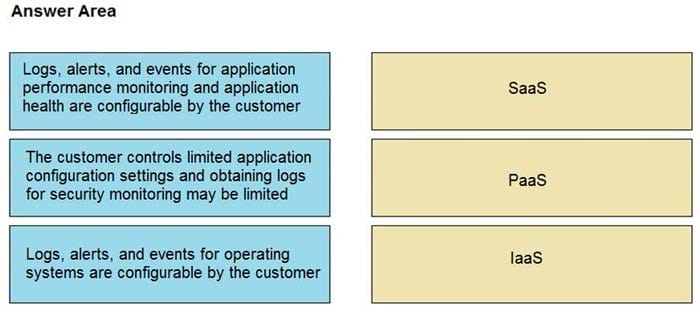
Correct Answer:
Q15: Which activity triggered the behavior analytics tool?
A threat actor attacked an organization\’s Active Directory server from a remote location, and in a thirty-minute timeframe, stole the password for the administrator account and attempted to access 3 company servers. The threat actor successfully accessed the first server that contained sales data, but no files were downloaded. A second server was also accessed that contained marketing information and 11 files were downloaded. When the threat actor accessed the third server that contained corporate financial data, the session was disconnected, and the administrator\’s account was disabled.
A. accessing the Active Directory server
B. accessing the server with financial data
C. accessing multiple servers
D. downloading more than 10 files
Correct Answer: C
…
Recommended Learning Resources (Internal & External Links)
- Official Cisco Exam Page (https://www.cisco.com/site/us/en/learn/training-certifications/exams/cbrcor.html)
- MITRE ATT&CK
https://attack.mitre.org/ - Splunk Documentation
(https://docs.splunk.com/Documentation) - Wireshark
- Leads4Pass (https://www.leads4pass.com/350-201.html)
- Security Onion
Final Summary: How to Pass on the First Attempt
To pass the 350-201 CBRCOR exam efficiently:
- Focus on real log interpretation
- Build scenario-based analytical workflows
- Master Splunk, Wireshark, Cisco Secure, and cloud logs
- Use Leads4Pass for realistic practice exam
- Understand MITRE ATT&CK techniques and their log footprints
350-201 is not just a certification—it is a career accelerator for anyone entering incident response, threat hunting, or SOC analysis.
With the rise of AI-powered threats and cloud-integrated attacks through 2026, professionals with hands-on forensic and response skills will remain in critical demand.